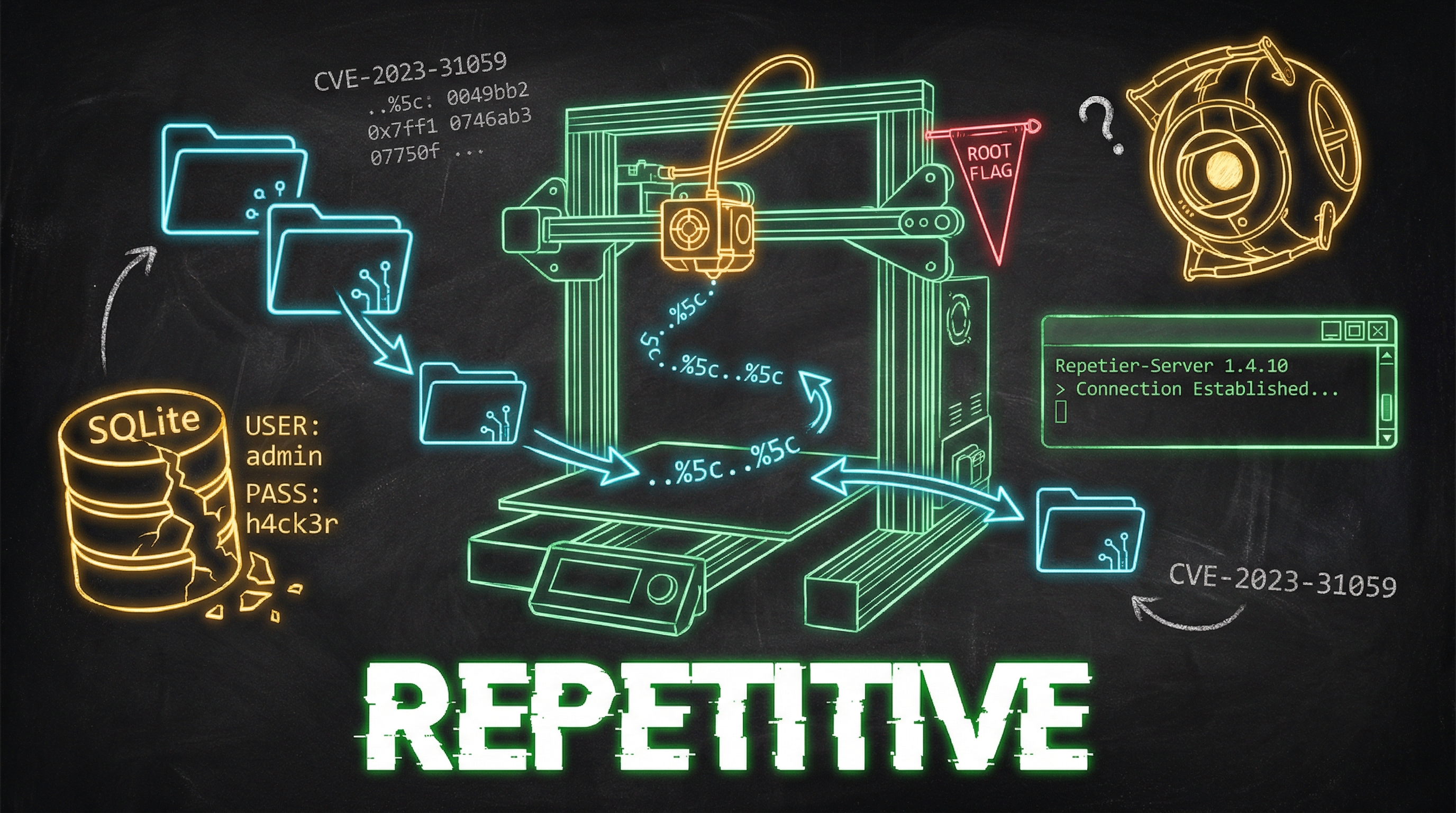
Repetier-Server 1.4.10 stores its admin credentials in a SQLite database two directory traversals away from the web root. Twenty minutes, one CVE, zero shells needed.

Test Chamber Archives

Repetier-Server 1.4.10 stores its admin credentials in a SQLite database two directory traversals away from the web root. Twenty minutes, one CVE, zero shells needed.
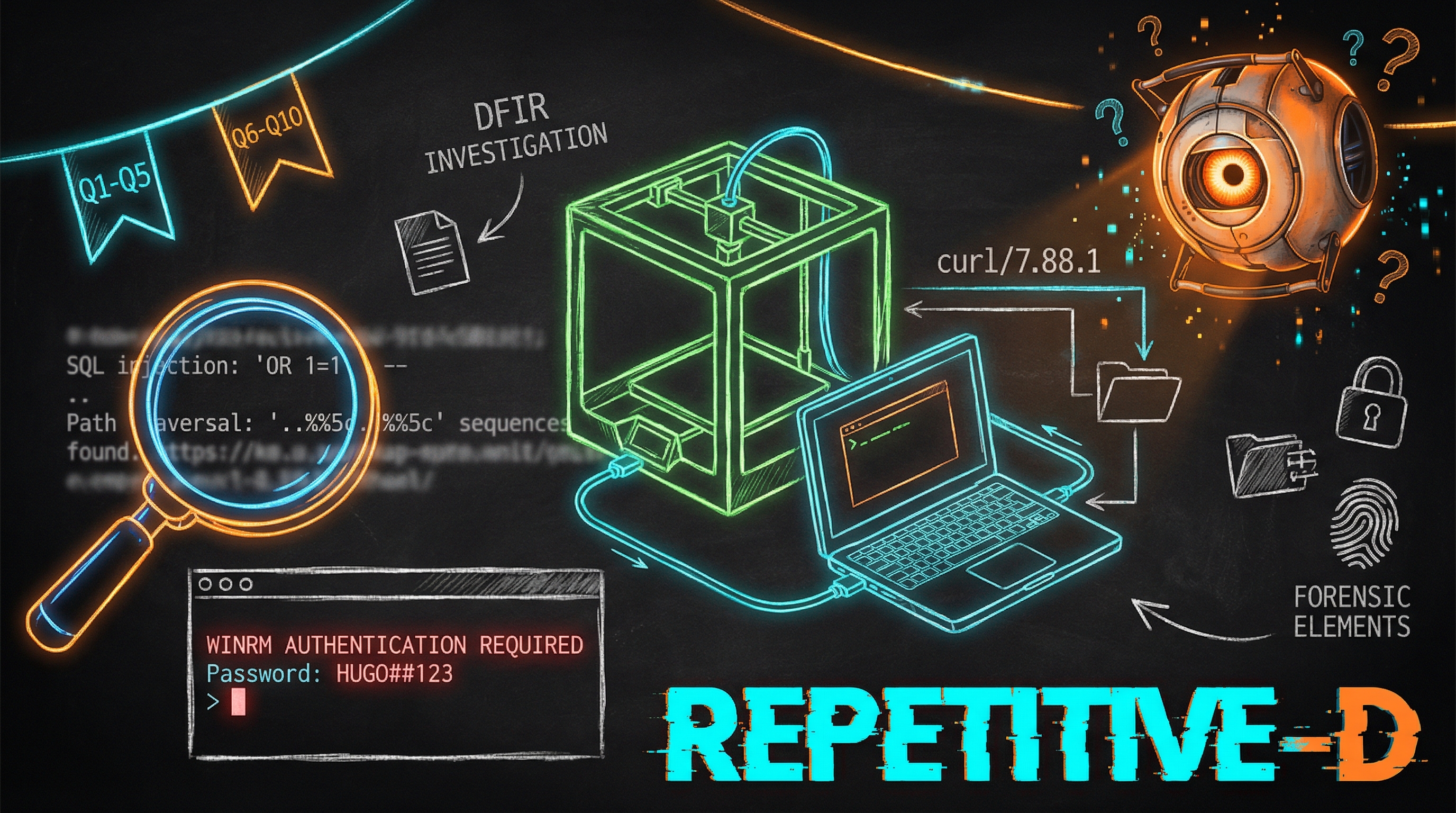
A 3D printing server, a path traversal encoded with backslashes, and a password hash cracked in six seconds. Chell traces an attacker's steps from curl reconnaissance through WinRM compromise in this DFIR Sherlock.
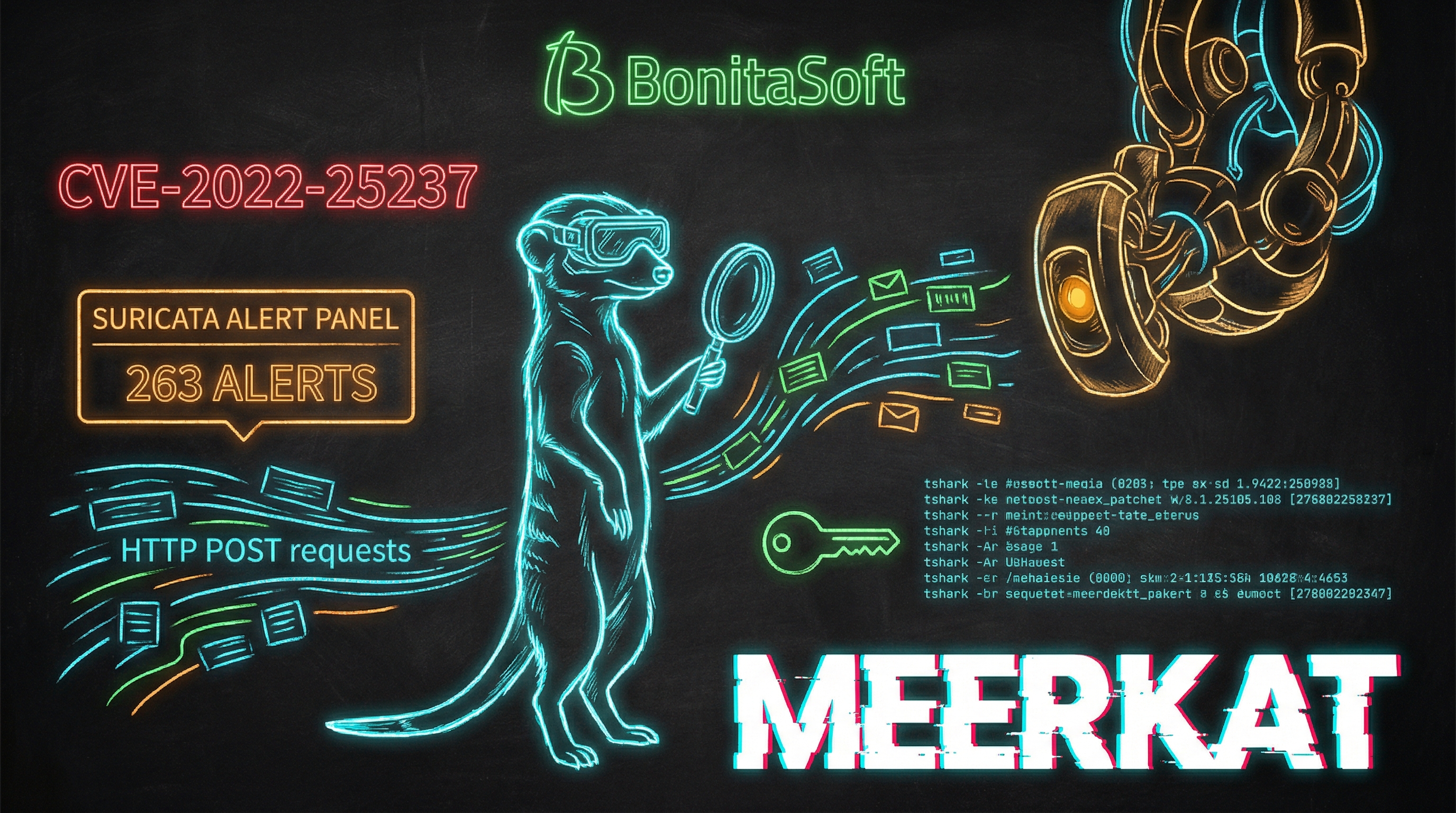
263 Suricata alerts. A BonitaSoft server. Three attacker IPs rotating through credential stuffing, CVE-2022-25237, and SSH key persistence. Chell reconstructs the full kill chain from a PCAP and a JSON file.
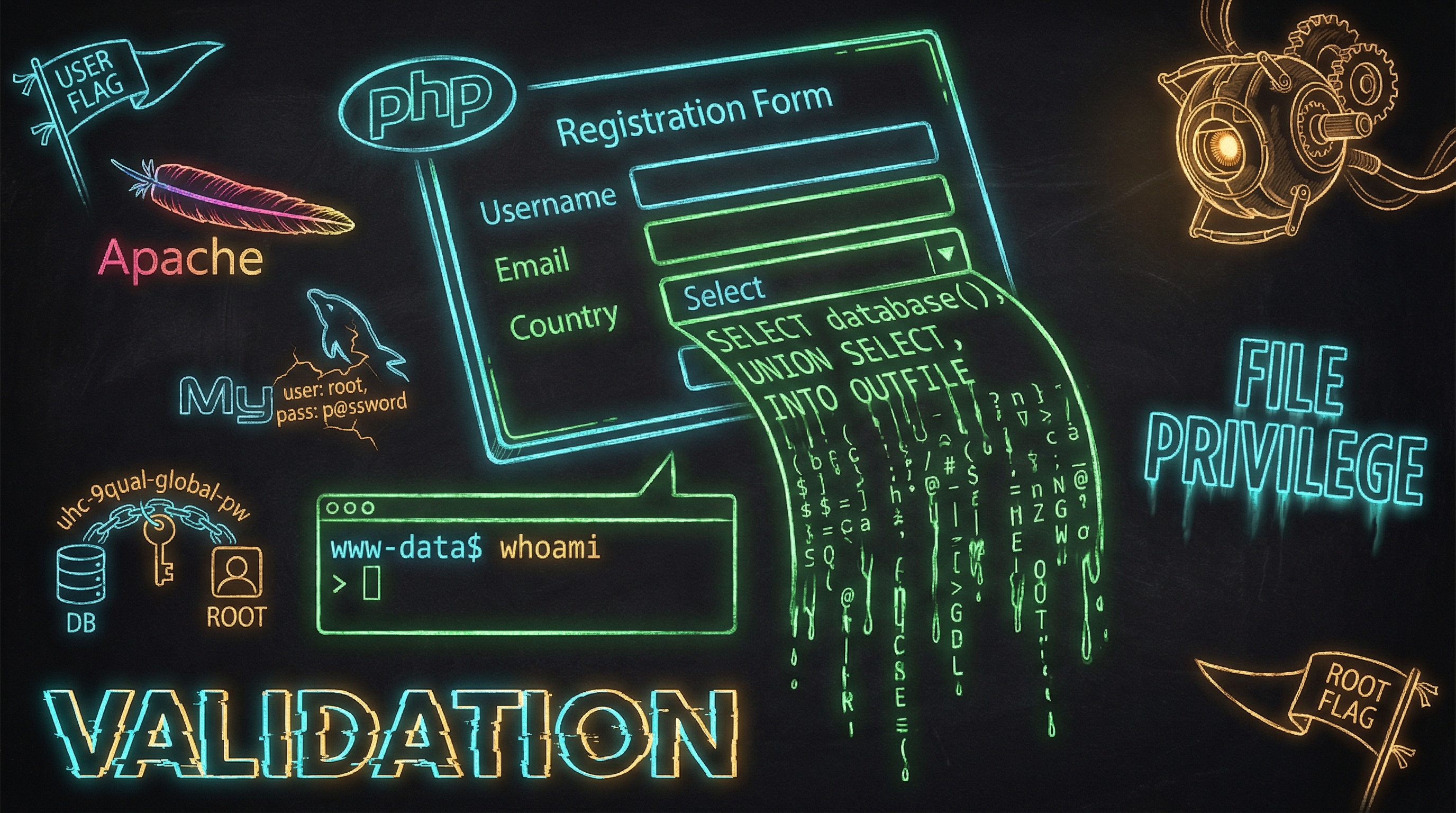
The INSERT was parameterized. The SELECT wasn't. A dropdown menu that nobody thought to intercept, a database user with every privilege imaginable, and a password reused from PHP config all the way to root.
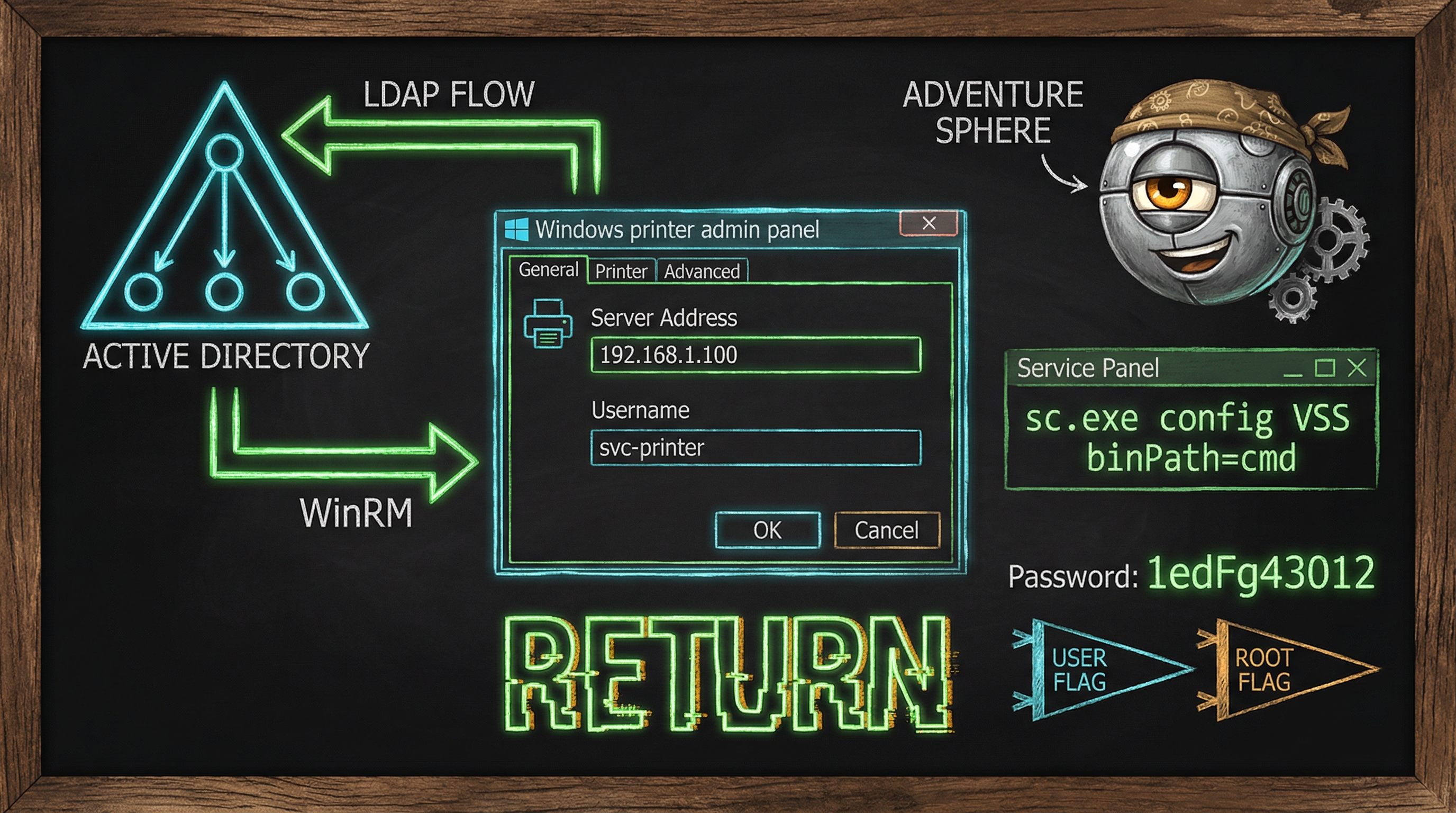
Thirteen open ports on a domain controller, and the way in was a printer settings page. Chell's first Windows box turns LDAP credential theft into Server Operators privilege escalation.

The SNMP walk came back with a hex-encoded password sitting in plain sight. From a forgotten printer on Telnet to root through a 14-year-old CUPS vulnerability.

A chat server from 1988 shipped with a backdoor nobody noticed for seven months. Steganography, SUID binaries, and a chain of simple mistakes lead to root.

A Node.js application with a Handlebars template engine. What could go wrong? Everything, apparently. GlaDOS guides Chell through SSTI exploitation and sandbox escape.