The Mission Briefing
Repetier-Server 1.4.10 stores its admin credentials in a SQLite database two directory traversals away from the web root. I know this because I read them. From my browser. Without logging in.
This was a guided box with seven questions, and the whole thing played out like a pop quiz on a single CVE. No shells, no reverse connections, no privilege escalation chain. Just one path traversal vulnerability, applied twice: once for credentials, once for the flag. The kind of box that teaches you how much damage a single unchecked file path can do.
Reconnaissance
The box had one port. One service. One question to start with: what runs on port 3344?
Repetier-Server. A web-based 3D printer management application built on Node.js with an AngularJS frontend. The nmap output showed the server version header as 1.4, but the guided questions wanted the full version number. I pulled the landing page directly.
Version 1.4.10. The HTML title, the CSS cache-busting parameter, the about text -- all three confirmed it. This was the exact version affected by CVE-2023-31059.
The Vulnerability
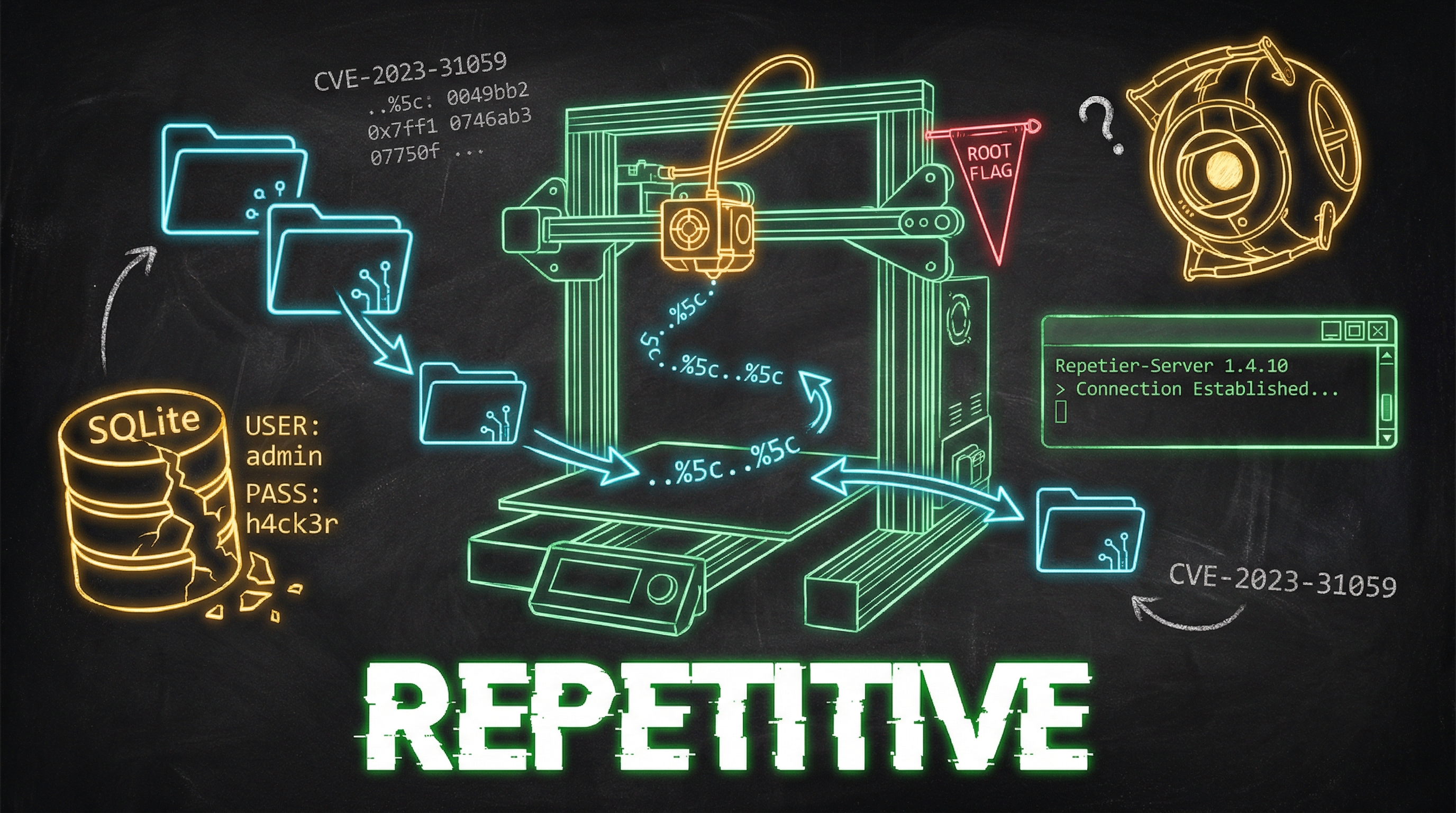
CVE-2023-31059 is a directory traversal vulnerability in Repetier-Server versions up to and including 1.4.10. The /views endpoint doesn't properly sanitize URL-encoded backslashes (..%5c), allowing an attacker to escape the web root and read arbitrary files on the system.
The technique is ancient -- URL-encoded path traversal dates back to the IIS Unicode bug of 2001. But the implementation here is specific to Windows paths. The %5c is a URL-encoded backslash (\), which on Windows serves as the directory separator. The web server decodes it after the path validation check, and suddenly you're reading files from anywhere on the disk.
Reading the Credentials Database
With the CVE identified, I knew exactly where to aim. Repetier-Server stores its user database in a SQLite file at ProgramData\Repetier-Server\database\user.sql. The path traversal through the /views endpoint with enough ..%5c sequences would reach it.
There it was. The entire user database, served up over HTTP. The Administrator account with an MD5 password hash of 3b3f51e91a93447f14249762f07fd384, full permissions (255), and an API key: bd03a7a4-91b6-4306-a594-832148e2d070.
The JavaScript analysis of the application revealed the hashing scheme: MD5(login + password). So the hash 3b3f51e91a93447f14249762f07fd384 is the MD5 of "Administrator" concatenated with the plaintext password. Not that I needed to crack it for this box -- the path traversal gave me everything I needed without ever logging in.
Capturing the Flag
No shell required. No privilege escalation. No lateral movement. The same path traversal that read the credentials database could read any file on the system -- including the flag on the Administrator's desktop.
Root flag: The flag is a liee15312ffbbbba4f45f3ae10f421bc6c5
The file was flag.txt, not the usual root.txt. One flag, one vulnerability, no authentication required. The entire attack surface was a single HTTP GET request with enough backslashes.
What I Learned
- URL-encoded path traversal on Windows -- The
%5ccharacter (backslash) is the key to Windows-specific directory traversal. Web servers that decode URL encoding after path validation are vulnerable to this classic technique. Always test both forward slashes and URL-encoded backslashes when probing for traversal on Windows targets. - CVE-2023-31059 in Repetier-Server -- Versions up to 1.4.10 allow unauthenticated file reads through the
/viewsendpoint. The fix requires upgrading past 1.4.10. If you run a 3D printer server, check your version. - SQLite credential databases are high-value targets -- When an application stores its user database in a predictable location (like
ProgramData\Repetier-Server\database\user.sql), any file-read vulnerability becomes a credential-theft vulnerability. The credentials included not just the password hash but the API key -- full programmatic access. - MD5(login + password) is not security -- Concatenating the username and password before hashing without a random salt means the same password for the same username always produces the same hash. Rainbow tables make this trivial to crack.
- Not every box requires a shell -- Sometimes the vulnerability gives you enough access to read what you need directly. Path traversal to arbitrary file read can be as devastating as remote code execution when the flag (or the sensitive data) is just a file on disk.